- Email: info [at] cyber72.com
- 6767560 Tel Aviv, Israel

As a business owner, you want to do everything you can to protect your company. That’s why it’s important to understand penetration testing and how it can help keep your business safe.
Penetration testing is a process of trying to gain unauthorized access to systems and data. It’s often used to find vulnerabilities in computer systems so that they can be fixed before attackers exploit them.
If you’re not familiar with penetration testing, this step-by-step guide will give you an overview of what it is and how it works. By the end, you’ll have a better understanding of whether or not penetration testing is right for your business.
Penetration testing is a vital part of any organization’s security strategy. By evaluating a system for potential weaknesses, penetration testing helps identify what must be done to protect confidential information, stop unexpected invasions, and prevent data breaches that can have serious consequences. A step-by-step guide to penetration testing provides an overview to security personnel of the assessments it involves and helps them adopt best practices in assessing their system for vulnerabilities. Each layer of a system is tested and appropriate steps are taken to ensure maximum protection from potential threats. By utilizing the necessary tools and guidance provided through penetration testing, organizations can hone the effectiveness of their cyber-security strategy in safeguarding their data assets.
Penetration testing is a comprehensive security assessment that can be used to test both physical and logical security. This type of assessment takes a critical look at the system and its components to identify potential weaknesses that an attacker might attempt to exploit. It also helps organizations stay ahead in the ever-evolving cyber threat landscape by identifying any vulnerabilities that could put sensitive data or infrastructure at risk. Penetration testing is an invaluable tool for improving overall security, as it allows companies to develop strategies that are customized to the unique security needs of the organization. So when you’re looking for ways to secure your business, penetration testing should be part of the equation.
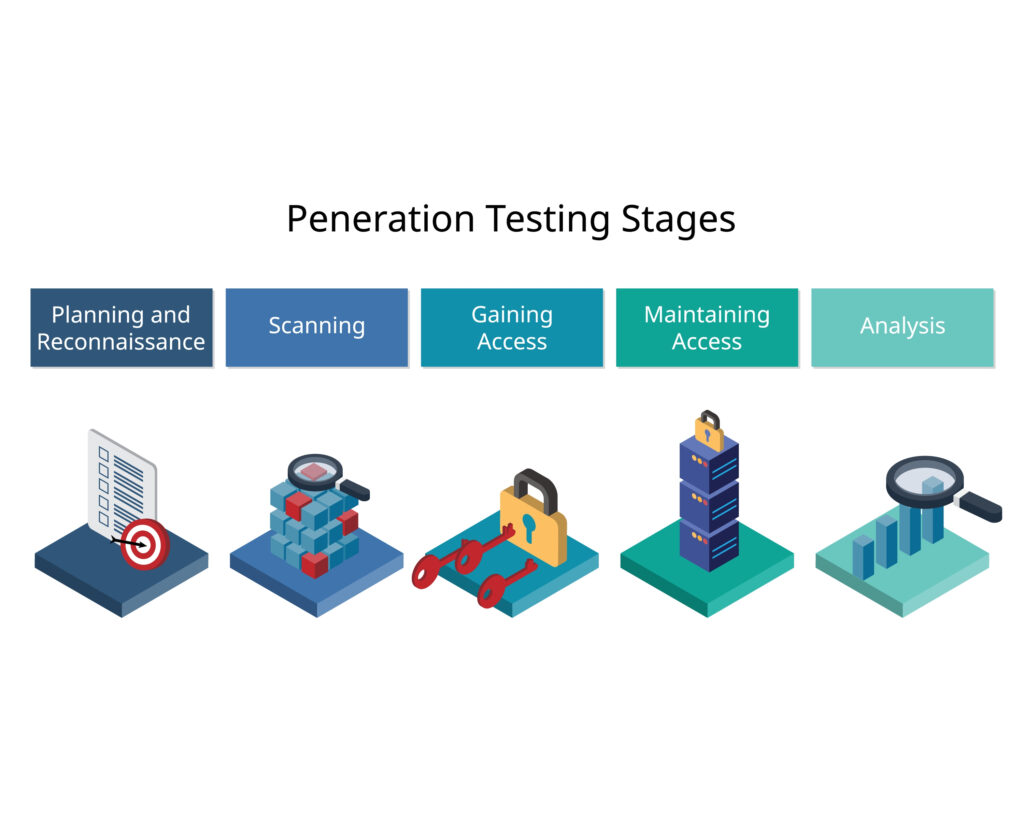
Physical penetration testing is a type of security test that takes place on-site. This type of testing examines the implementation and characteristics of physical security controls at the site, such as the strength of the door and window locks and other physical barriers. On the other hand, logical penetration tests are carried out remotely and typically focus on finding weaknesses in network systems, including network firewalls, servers, computers and applications. These tests are conducted using automated tools to search for vulnerabilities throughout the system and to identify access points. In both cases, penetration testers pinpoint areas where there may be potential risks and suggest corrective actions to increase protection against threats.
Penetration testing is the practice of carrying out a simulated attack on your system to identify potential weaknesses in its security. The goal of such an attack is two-fold: to pinpoint any security vulnerabilities and flaws, and to ensure that such issues can be addressed before they become exploited by malicious hackers or criminals. By engaging in this type of activity regularly, organizations can guarantee that external threats don’t have the opportunity to breach their systems and steal confidential data or cause disruption. Ultimately, it provides peace of mind that even with outside threats looming, the system remains secure against intrusions.
Conducting a successful penetration test requires technical skills and knowledge. Firstly, you will need to have access to the targeted system, whether it is in your local environment or remotely. Secondly, being able to understand common attack methods is essential. This means having an extensive knowledge of the different kinds of attacks that can be employed when attempting to hack into a system. Understanding common vulnerabilities such as outdated software and weak passwords is also important in order for the penetration test to be successful. By properly preparing for their assessments and ensuring that both physical and digital security are considered, an individual or company can keep their system safe from would-be attackers.
Penetration testing is a methodical process of identifying security vulnerabilities that can be exploited within IT systems. After gaining access to the system, an in-depth analysis must be conducted in order to assess its security posture. This involves running dedicated scripts to enumerate the systems and services running on the given system. These scripts allow testers to detect any known vulnerabilities that can be taken advantage of and are normally found in unpatched software or applications that have not been configured properly. Such information can then be used by the tester(s) to further exploit the system and gain access to sensitive data or other resources.
Penetration testing is a powerful security tool that can be used to find vulnerabilities in both physical and logical systems. By enumerating the systems and services that are running on a target system, penetration testers can identify weaknesses that could be exploited by attackers. By conducting penetration tests regularly, organizations can stay one step ahead of the attackers and keep their systems safe.
Proper preparation and knowledge of common attack methods are essential for a successful test to be conducted. By being proactive about security, organizations can reduce the risk of data breaches, downtime, and other costly issues that could arise from an unsecured system.
By making sure that the network is secure and protected against external threats, organizations can ensure their systems remain safe and secure.
Finally, organizations should consider investing in a vulnerability management solution to automate the process of identifying security flaws before they become exploited. Vulnerability management solutions provide real-time scanning of systems and applications to detect known vulnerabilities so that they can be patched quickly before they are taken advantage of by malicious actors. These tools also offer automated remediation options that make it easier for IT staff to apply the necessary updates or patches. By having a comprehensive vulnerability management strategy in place, organizations can increase their protection against potential threats and have peace of mind knowing their data remains safe from external attacks.
The goal of penetration testing is to identify and exploit weaknesses within a system to gain access. The process requires technical skills, knowledge of common attack methods, and the right tools to be successful. By preparing for their assessments and understanding security best practices, organizations can protect their systems from malicious actors and remain secure against external threats. Furthermore, by investing in a vulnerability management solution they can easily detect security flaws before they become exploited. A comprehensive approach to cyber security is key to keeping data safe and secure from attackers. With proper preparation and utilizing the right strategies, an organization can be confident that its network remains safe from potential intrusions.
Penetration testing is a powerful tool that organizations should use to protect their systems and data from potential attacks. With the right preparation and knowledge, organizations can reduce their risk of vulnerabilities and gain an edge on cyber threats. By understanding the importance of security best practices and investing in solutions such as vulnerability management, organizations can feel confident knowing their network remains secure. Ultimately, by taking proactive measures to protect themselves, businesses can ensure their data is kept safe from malicious actors.
By using the proper strategies and tools for penetration testing, organizations can identify weaknesses within their system before they become exploited. By understanding common attack methods and having the right tools at their disposal, testers will be able to detect any vulnerabilities and proactively patch them before they become an issue. This will help ensure that the system remains safe from malicious actors and reduce the risk of data breaches, downtime, and other costly issues that could arise from an unsecured system. Vulnerability management solutions can also be used to automate the process of detecting security flaws and applying patches quickly in order to keep the network secure. By taking a proactive approach to security, organizations can protect their systems from external threats and have peace of mind knowing their data is kept safe.
Ultimately, penetration testing is a powerful security tool that should be utilized by organizations that want to stay one step ahead of attackers and remain secure against potential intrusions. With proper preparation, knowledge of common attack methods, and the right tools, testers can detect and exploit weaknesses within a system before they are taken advantage of by malicious actors. By investing in solutions such as vulnerability management they can further automate the process of detecting and patching security flaws quickly. With the right strategy in place, organizations can ensure that their data remains safe from external threats and have peace of mind knowing it is kept secure.