- Email: info [at] cyber72.com
- 6767560 Tel Aviv, Israel
Last updated: Dec 6, 2022
You’re always looking for ways to improve your security as a company. One way to do that is by conducting pen or penetration tests. But what are the different types of pen tests? Read on to find out.
Types of penetration testing include a web applications, network security, wireless network, social engineering, and mobile application.
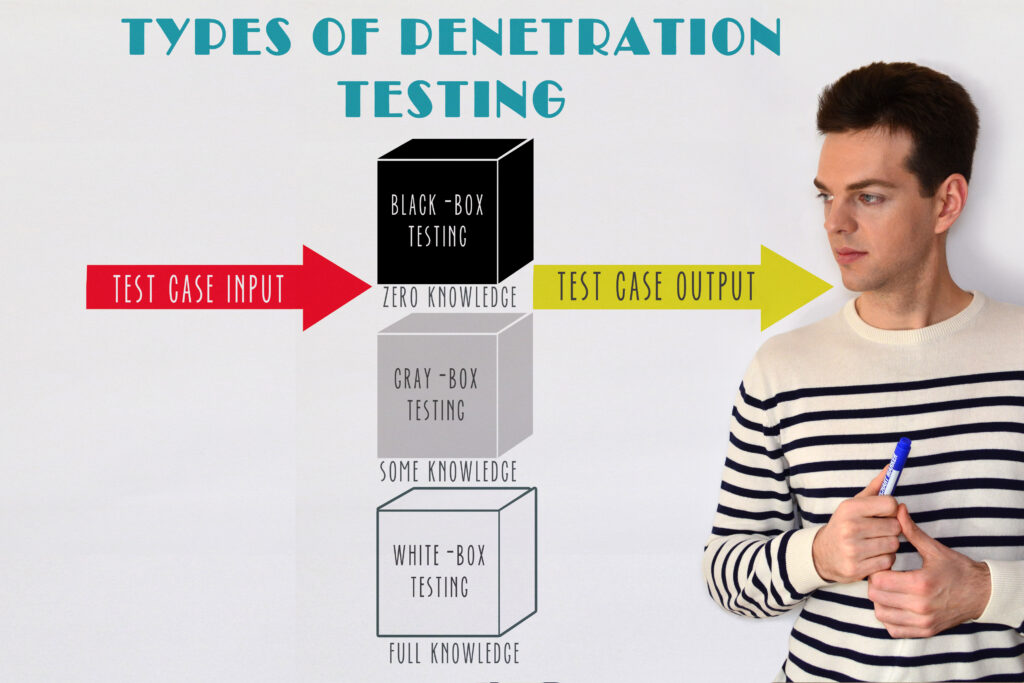
Have you ever been presented with the challenge of evaluating a system without knowing anything about it ahead of time? This is the essence behind black box testing – a process in which testers are kept completely in the dark about the system being tested. Even experienced testers can find themselves lost in these situations, as they have no access to any underlying code or design plans. Still, resources like logical reasoning and creative problem-solving can help to uncover issues even with this lack of background knowledge. Compared to other approaches, black box testing offers a new way of scrutinizing systems from an external point of view, providing keen insights into how users may interact with it and ultimately detect unforeseen problems that could derail its success. For any curious problem-solvers out there looking for a puzzle, this form of testing might just be the answer!
White box testing is a great way to really get inside a product. Unlike other forms of testing, it doesn’t require the tester to use the product in any particular way – they can literally open up the box and rummage around inside. White box testers are provided with full access to the system, so they’re free to explore, experiment, analyze and try different paths through the application. This type of test might not reveal all the flaws in the system, but it allows testers to exercise their curiosity while helping inform decisions and uncover unexpected issues. For tech teams looking for an innovative approach to debugging their systems, white box testing is a great place to start. It might not provide definitive answers but at least it will be interesting!
Gray box testing is the happy medium between white box and black box testing, where the tester has a few more clues than in the latter but far less information than in the former. With gray box testing, testers are able to dig around a bit beneath the surface level of a system or application and get some insights into what’s going on. For example, they might be privy to the internal logic of a software product, receive high level overviews about the structure of an application’s codebase, or have access to functional design documents that provide valuable data to test against. In this way, testers are still largely in blue jeans and tee shirts during their exploration rather than diving full-on into developer clothing – like white box testers do – but they can glean insight beyond simple user sessions like black box testers often do. Whether you’re dealing with web applications or embedded software systems, gray box testing can provide invaluable insight during verification processes. It’s simply a matter of unlocking the door that opens up just enough to see what lies inside without getting too close to certain details you’re better off leaving alone!
If you’re like most business owners, you’re always looking for ways to improve security. One of the best ways to do that is by performing an open-box pen test. In this blog post, we’ll discuss what an open-box pen test is and why you need to perform one. We’ll also provide some tips on how to get started.
A closed-box pen test, also known as a white-box test, is a penetration testing method that uses information about the system that is not available to the attacker, such as the source code, to identify and exploit vulnerabilities. This type of testing is more thorough than an open-box test, which relies on publicly available information and can be used to identify more subtle vulnerabilities.
A covert pen test, also known as a black-box test, is a penetration testing method that uses information about the system that is not available to the attacker, such as the source code, to identify and exploit vulnerabilities. This type of testing is more thorough than an open-box test, which relies on publicly available information and can be used to identify more subtle vulnerabilities.
An external pen test is a penetration testing method that uses publicly available information to identify and exploit vulnerabilities. This type of testing is less thorough than an internal pen test, which uses information about the system that is not available to the attacker, such as the source code.
An internal pen test is a penetration testing method that uses information about the system that is not available to the attacker, such as the source code, to identify and exploit vulnerabilities. This type of testing is more thorough than an external pen test, which uses publicly available information.
Red teaming is the wild west of cyber security – and arguably one of the most exciting roles you could take. Imagine it: forming a coordinated team tasked with the sole purpose of breaking into a system. For computer engineers and security testers, this is an incredible opportunity to exercise their skills and knowledge – as well as create some enjoyable chaos along the way. However, although red teaming can be a lot of fun, it should not be taken lightly; if done incorrectly, your team’s “brute force” tactics could easily bring down entire systems! The key to successful red teaming lies in having a robust plan beforehand that considers every possible angle – and an equal amount of creativity and persistence once in. Ultimately, red teaming requires a good mix of technical abilities combined with strategic thinking – so if you have what it takes, maybe you should give it a try! After all, there are few jobs that offer such satisfying results — those iconic success messages may soon become your new favorite thing.
The term ‘blue team’ may have you envisioning a superhero ensemble of IT security professionals, but there is much more to it than meets the eye. A blue team has one specific purpose – to test the security of your systems. They actively search for vulnerabilities while identifying areas where malicious actors can gain access. Rather than attacking a system, they “defend” it, using tools and techniques to protect your data both online and in physical stores. Of course, being able to anticipate attacks before they happen means that a blue team must remain up-to-date on the latest threats out there. This means that blue teaming is an ongoing process that requires knowledge not only of your systems and processes, but also what malicious actors might be scheming in order to breach them! It’s all in a day’s work for these security warriors – daringly facing down any bad guys with one hand on their keyboard and the other ready to take action!
In the world of cybersecurity, red teams and blue teams battle it out to protect fragile systems from threats lurking on the outside. However, a desired outcome of these rivalries is for them to work together, creating what is known in the industry as purple teaming. The idea behind this method is deceptively simple – have both teams collaborate on testing and validating their security system. Red teams look for weaknesses even in unexpected places, while blue teams shore up vulnerable points before they are exploited. When these two come together, it can be more effective than either working alone; an idea that many hackers find quite disconcerting! Purple teaming acts almost like an insurance policy, giving organizations peace of mind that their security is being tested from all angles and any potential weakness has been checked and remediated. In essence, it provides an extra layer of security that can help prevent future malicious attacks or data breaches. That’s why purple teaming needs to be part of your security approach – why risk leaving any weakness uncovered? With red and blue working together, you may find yourself seeing nothing but purple streaks in the sky!
Conclusion paragraph: In the ever-changing world of technology, it’s more important than ever to make sure your systems are secure. Whether you’re using black box or white box testing methods, it’s crucial to have a team of experts who can help you find and fix any vulnerabilities in your system. At [company name], we specialize in helping businesses just like yours stay safe online. Contact us today to learn more about our security services and how we can help keep your business protected from cyberattacks.
Pen tests can be performed by anyone with the right skill set, but it’s typically done by a specialized team of experts. At cyber 72, we have a team of experienced professionals who are dedicated to helping businesses stay safe online. Contact us today to learn more about our pen testing services and how we can help you secure your systems from cyberattacks.